Deceive cross references analysis (XREF)
One of the usefull thing in reverse engenering is xrefs (cross-references), with a complet analyse of all the PE, variables and function addresses can be linked to functions where they are called or used. This simplify drasticly the reverse engenering, but xrefs can be a problem in case of security check. If you have a big executable and you want to look at the license check system, a string like “Check License” or “Enter License” can be find easily and the xrefs associated to him will show you directly what you wanted to find.
Basically, xrefs in commun tool just make a link between the place where the address is used and the data at this address.
So the simple trick that we could use is just to manipulate the address where is called to unmatch with the real data location.
The “tricks” can be used only if ALSR is disable (we need to know static addresses in executable) and yes it’s cold be a security issue is the application is important (read documentation about it), but it’s a simple way to limit xrefs.
If you used packing you have to consider this when you write addresses in the executable.
Note : the objective is to deceive static analysis
POC
To explain my point, I will take this code :
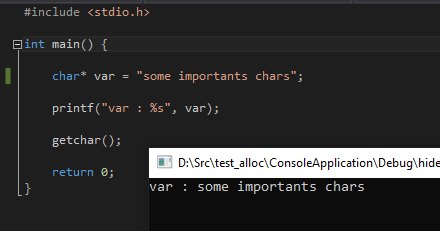
When we reverse the executable, we can clearly see where the string is called and, by logic, when we look at the main function, we see exactly how it will be used
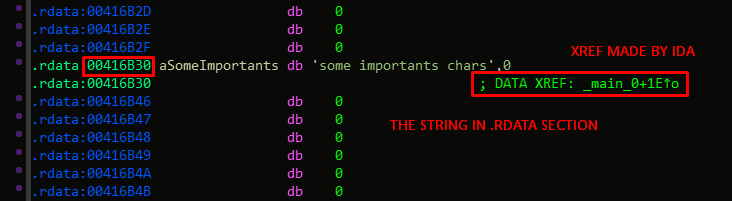
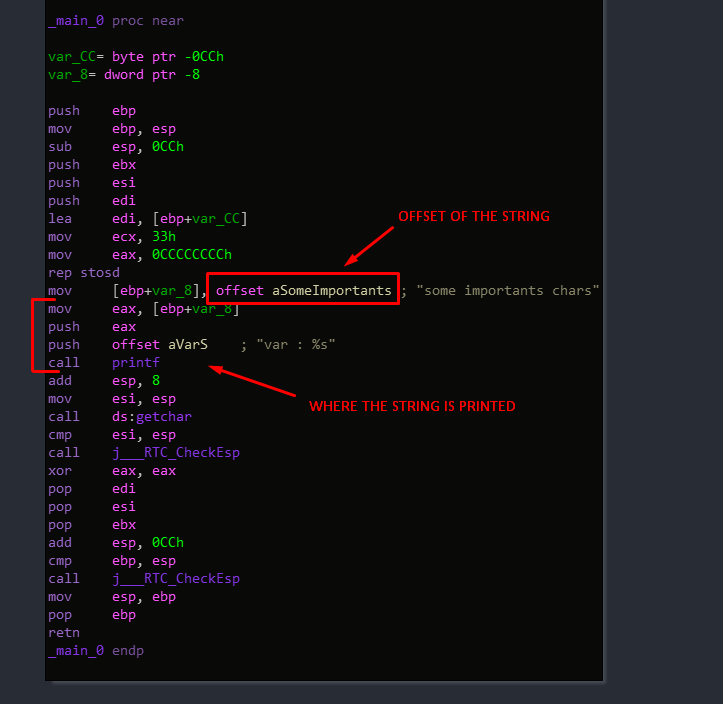
As we can see IDA made a link between the address used in the mov instruction, and the data in the .rdata section at the same address as the mov instruction one.
To deceive IDA’s xref, we have to modify the address used in the mov instruction to unmatch in raw file when IDA analyse it, but make it correct at the execution.
The trick is to know the memory address of the variable, and, at execution, grab its value from an obfuscated mechanism that hide the address.
So we need to know the address of the variable (ASLR Disabled), obfucate it to be not liked in the executable by IDA, and get the value at this address to use it in the printf.
So first, we have to make an obfuscated algorythm that is allready setup in the assembly and where we just have to modiy values after compilation.
NOTE : Again my point of view is from the source code in my POC, but with a program that is able to make code caving, code injection and manipulation, we can do it automaticly without thoses steps. And so, in my case, don’t forget that a little change in the code at compilation can recalculate all variables addresses, so we have to cosider that in the obfuscation.
I will take a simple x * y - z algorithm and I will write the values after compilation
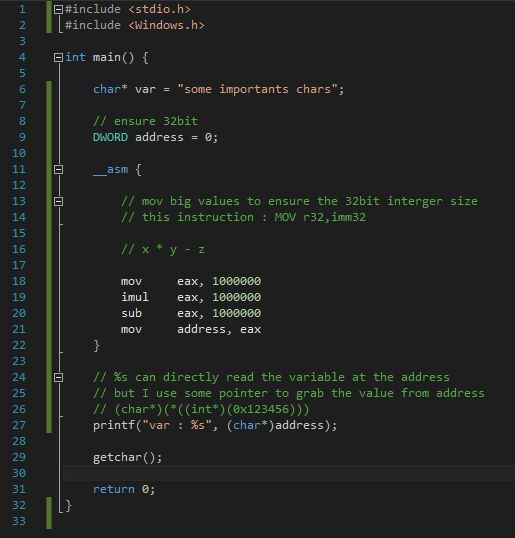
Let’s write the address. (create tool don’t write them manualy)
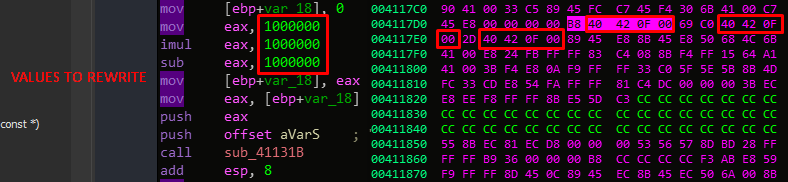
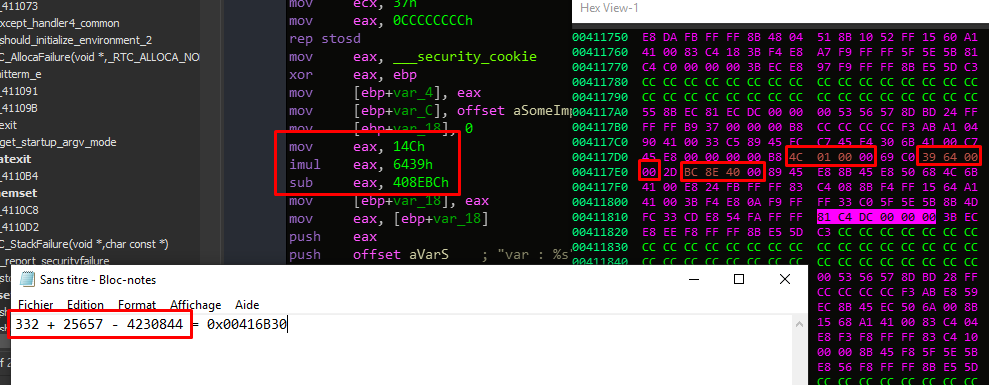
And as result
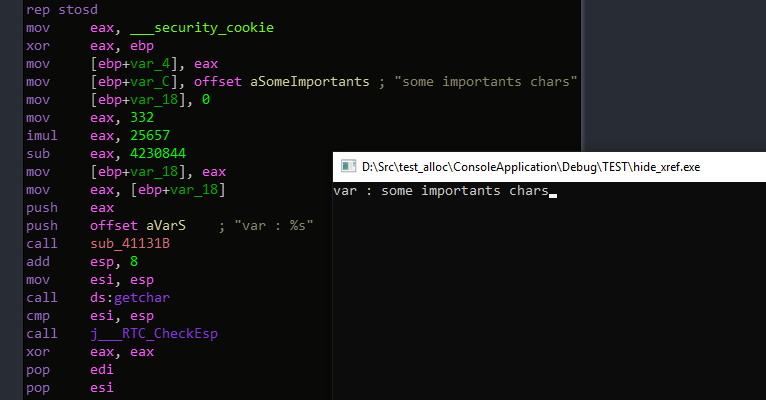
Its working :D
But we see two more little things, the “some chars” string is defined in the function, so the function store its address in the bottom of the function, also this function make an additionnal mov to eax to use the variable, so we have to make a more clear code.
Let’s fix
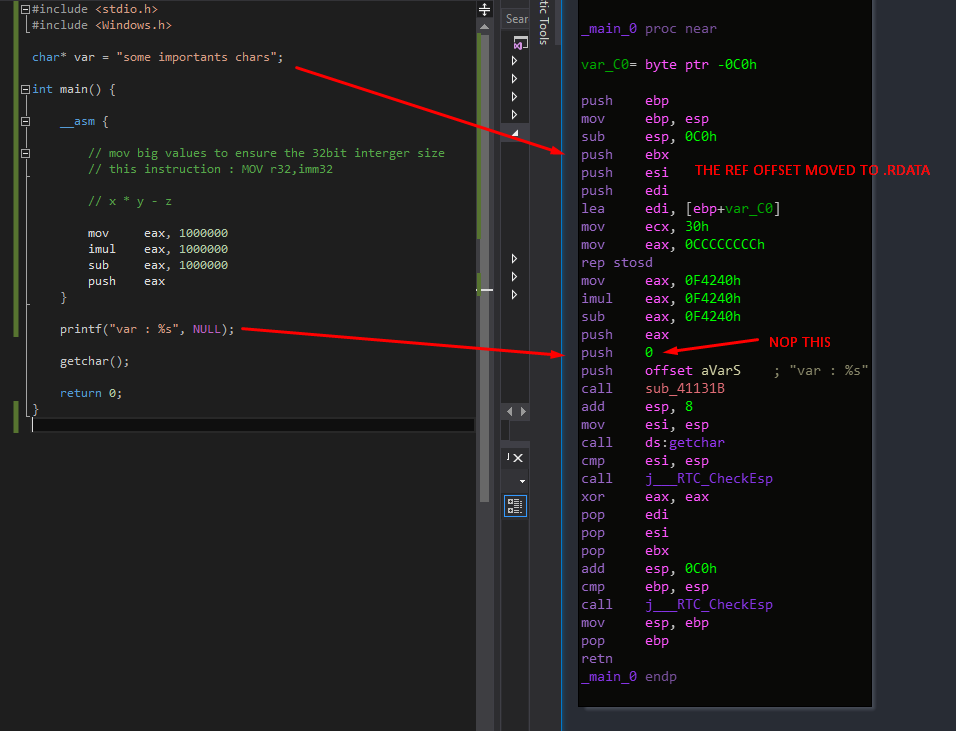
(the inline asm of VC++ push the final value at compilation, so I have to nop the push :/ )
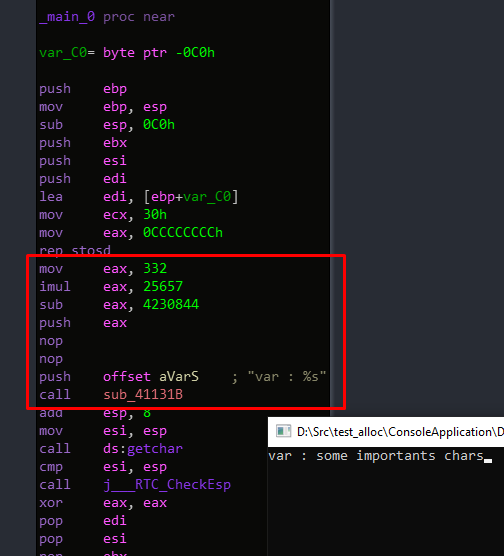
(I’ve push manualy the number and nop the push 0 of the NULL)
I could make code caving but I will make this in an other post.
So now the xref is no longer made by IDA :D
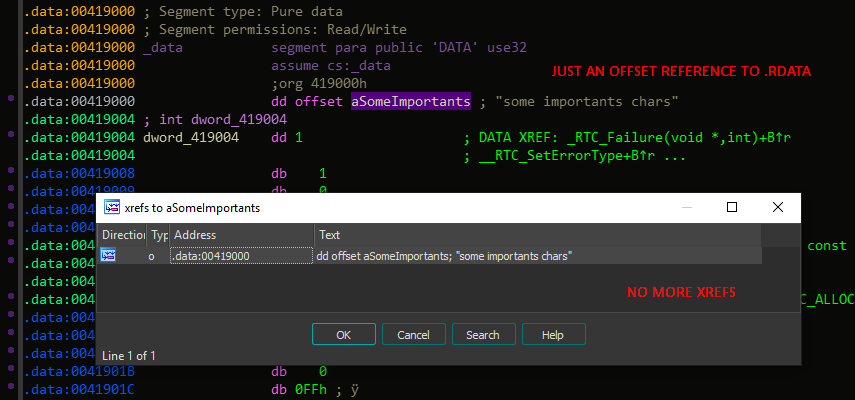
So now the only limit is your imagination about creating complex obfuscation.
In a little tool like this, it can be found with a little bit of knowledge, but in a big tool, it could be hard